
Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.
Abstract: In the latest Bluetooth 4.2 core specification, a new feature is supported that can help Bluetooth users protect their privacy by periodically changing the random address of the Bluetooth device to prevent their devices from being hacked or It is the eavesdropper who steals through radio frequency interception and data analysis. This privacy feature does not work during the discovery process of the GAP (Generic Access Profile), but protects the device's whereabouts after the connection is established. Once the device adopts the concept of a variable random address, the privacy of the device user can be well protected. This article will focus on the technical details of privacy protection in the Bluetooth 4.2 core specification.
This article refers to the address: http://
In our daily wireless communication devices, MAC addresses are included. The MAC address is unique. Usually in network communication, the MAC address is used as a device symbol. The MAC address is mostly allocated by the manufacturer of the device and stored in the device. If there are two devices in the network with the same MAC address, then there will be problems with network communication, so the manufacturer of the device is very careful when assigning the MAC address to ensure the uniqueness of the address. If we want to get the MAC address of the device is very simple, when we open the smartphone or tablet, you can easily find the MAC address of the device in a device similar to the "device management" interface, and some devices, such as wireless Routers, their MAC addresses are printed on the back of the device. At the same time, we can also obtain the MAC address of the device in other ways.
Let's imagine that when we travel through the city on public transportation every day, when we shop at a mall or have a meal with friends at a restaurant, your smartphone can help you pay, order and navigate. If your smartphone is connected to a network hotspot for Internet access, it may broadcast its MAC address during this series of processes. We mentioned the uniqueness of the MAC address in the network communication. You are the user of the smartphone. The MAC address of this smartphone represents your identity during the wireless communication process from a certain perspective. . Therefore, there is a possibility that some malicious people can obtain the MAC address of your smartphone for data interaction through some other wireless communication devices and record the date, time and related location of the MAC address. Then your whereabouts can be monitored, as shown below.
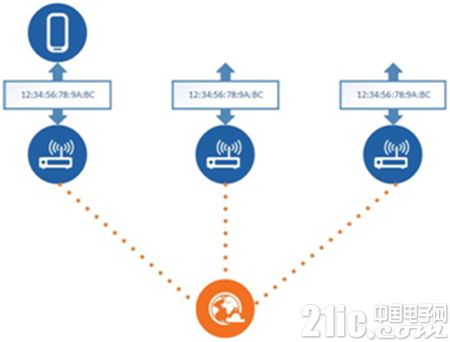
Using Bluetooth technology, you may also face this problem. Therefore, in the Bluetooth 4.2 core specification, a solution to the above problem is proposed. To understand the solution, first of all, start with the address of the Bluetooth device. Similar to other wireless communication technologies, Bluetooth devices also have their own device addresses. In the core specification of Bluetooth, we usually call it BD_ADDR (Bluetooth Device Address). BD_ADDR will play a role in Bluetooth devices such as connection and pairing. The role of device identification. For Bluetooth devices, you can use the Public Address or the Random Device Address. However, whether you use a public address or a random address, their address length is 48 bits, which is 6 words. Section.
The composition of the public address consists of two parts, one part is the company ID, which needs to be paid by the IEEE registration authority. The company identification code is 24 bits long and is 24 bits high at the 48-bit device address. The other part is The company Assigned ID, which is also 24 bits in length, is at the lower 24 bits of the 48-bit device address, as shown in the following figure.

Public address
In addition to public addresses, Bluetooth devices can also use random addresses for related network operations. There are two types of Bluetooth random addresses: Static Device Address and Private Device Address. Because of the static address and the subject of this article - how to use Bluetooth 4.2 to protect privacy is not great, here we focus on the private address. In the definition of private address, there are two subclasses: Non-resolvable Private Address and Resolvable Private Address (RPA). The so-called unresolvable private address is that the Bluetooth device address changes periodically, and this address cannot be resolved by other devices. We can think of it as a random number. Unresolvable private addresses protect user privacy because changing device addresses prevent any device from tracking users by recording Bluetooth device addresses, but this protection also means that trusted devices cannot. The true identity of the Bluetooth device, so we focus on the resolvable private address. As shown in the figure below, the device address of the smartphone is constantly changing, so even if the device address is obtained, the real identity of the device cannot be resolved unless there is some kind of resolution key.
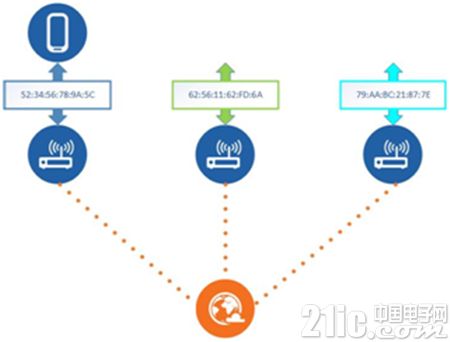
The resolvable private address means that the Bluetooth device address BD_ADDR is constantly changing, which protects the user's privacy from being tracked. At the same time, because it is resolvable, the pairing device (Pair Device) can resolve the Bluetooth through this private address. The true identity of the device. So, we need to understand how a resolvable private address is generated?
Suppose there are two Bluetooth devices, namely device A and device B. After the two Bluetooth devices A and B establish a connection, the two Bluetooth devices can exchange their respective identity resolution keys IRK (Identity Resolving Key). IRK), the identity resolution key IRK-A of device A, and the identity resolution key IRK-B of device B. Assuming device B uses a resolvable private address mechanism, device B needs to periodically generate a resolvable private address. The following figure shows the structure of a resolvable random address, where the upper two bits of the resolvable random address are 0 and 1, respectively, as identifiers of the resolvable address.
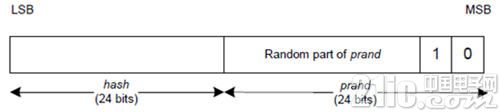
Resolvable private address
When device B needs to generate a random address, it internally generates a random number prand. Based on the prand random number, device B needs to use the hash hash algorithm to generate another part of the resolvable random address, hash. The prand random number and the hash hash occupy 24 bits respectively, and the calculation formula is:
Hash hash = ah (IRK-B, prand random number)
The function ah is described in detail in the Bluetooth 4.2 core specification, Volume 3, Part H, Section 2.2.2, and will not be described here. After device B has a prand random number and a hash hash generated based on the prand random number, the resolvable random address RPA can be generated by shifting the phasewise AND.
RPA= hash|| prand
So how does device A resolve the RPA? When device A receives a Bluetooth device address BD_ADDR and the address identifier of the address indicates that it is a resolvable random address, device A first splits the address into prand random numbers and Greek hash. Next, it uses the IRK-B obtained when paired with device B to generate a local hash localHash via function ah.
localHash = ah(IRK-B, prand)
If the generated local hash localHash is equal to the hash hash obtained by the split, the address is the resolvable random address generated by device B; if not, the resolution fails. Device A can resolve this address by using the IRK of other devices it acquires. The figure below is a flow chart of address resolution.

Address resolution process
Therefore, for the resolution of a resolvable random address, we can think of it as an exhaustive process. When any device receives a resolvable random address, it will hash the resolvable random address with all the IRKs stored locally. If the parsing process terminates, the real identity of the address can be resolved. All IRKs cannot resolve this address, then the parsing fails.
Through the above method, the Bluetooth device can protect the privacy of the device by using a resolvable random address to protect the privacy of the device user. After the resolvable random address is used, the address of the Bluetooth device is periodically changing, so even if the address of the Bluetooth device is obtained by other means, the device cannot be tracked by the time and address of the device address. Only trusted devices that have completed the identity resolution key IRK interaction through the pairing process can parse the resolvable random address.Acrylic Anti Blue Light Filter, Blue Light Screen Protectors, Blue Light Filter For Pc, Anti Blue Light Filter
May 15, 2024
March 02, 2024
March 02, 2024
Contactar proveedor
May 15, 2024
March 02, 2024
March 02, 2024

Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.

Fill in more information so that we can get in touch with you faster
Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.